open source digital security

In response to the election of the fascist capitalist Donald Trump in the USA and the rising tide of the far-right in countries across the world like Israel, the Netherlands, and the UK, lots of people will be looking for secure software solutions for communication and storage of information that they don’t want the state to monitor. The clear choice is open source software: as security expert Bruce Schneier has written, “[i]n the cryptography world, we consider open source necessary for good security; we have for decades. Public security is always more secure than proprietary security. It’s true for cryptographic algorithms, security protocols, and security source code. For us, open source isn’t just a business model; it’s smart engineering practice.” More than that, given the involvement of tech-focused billionaires like Jeff Bezos and Elon Musk in getting Trump elected, you simply cannot trust software companies like Amazon, 𝕏, Meta, or Google. A corporate proprietary software company will side with a far-right state in a heartbeat.
This post outlines my approach to digital security using a range of open source software tools. I trust all the software recommended in this post but your threat model might be different to mine and so may require a different approach. I’ll also recommend European Alternatives generally which is a useful catalogue of software and digital services which are based in Europe rather than the USA: these aren’t all open source but it does helpfully flag which alternatives for popular services are open source and which are proprietary.
communication
Communication is perhaps the area where it’s most important to practice good security. It is simply a fact that the governments of the USA, UK, Australia, Canada, and New Zealand spy on the private and public internet communications of their citizens with the cooperation of companies like Apple, Google, Microsoft, and Meta. For video conferencing communication more specifically, you can see my previous post on open source video conferencing solutions.
Signal is what you should be using for private messaging in place of WhatsApp, iMessage, Facebook Messenger, or the DMs of whatever social media platform. It offers secure end-to-end encrypted messaging, voice calls, and video calls. Telegram is another similar messaging service but their security is not as robust as Signal. Signal is available from Google Play or Apple’s App Store with desktop versions that sync with your mobile device. Signal is distributed under a AGPL-3.0 license and developed by the Signal Technology Foundation whose mission is to "protect free expression and enable secure global communication through open source privacy technology."
web browsing
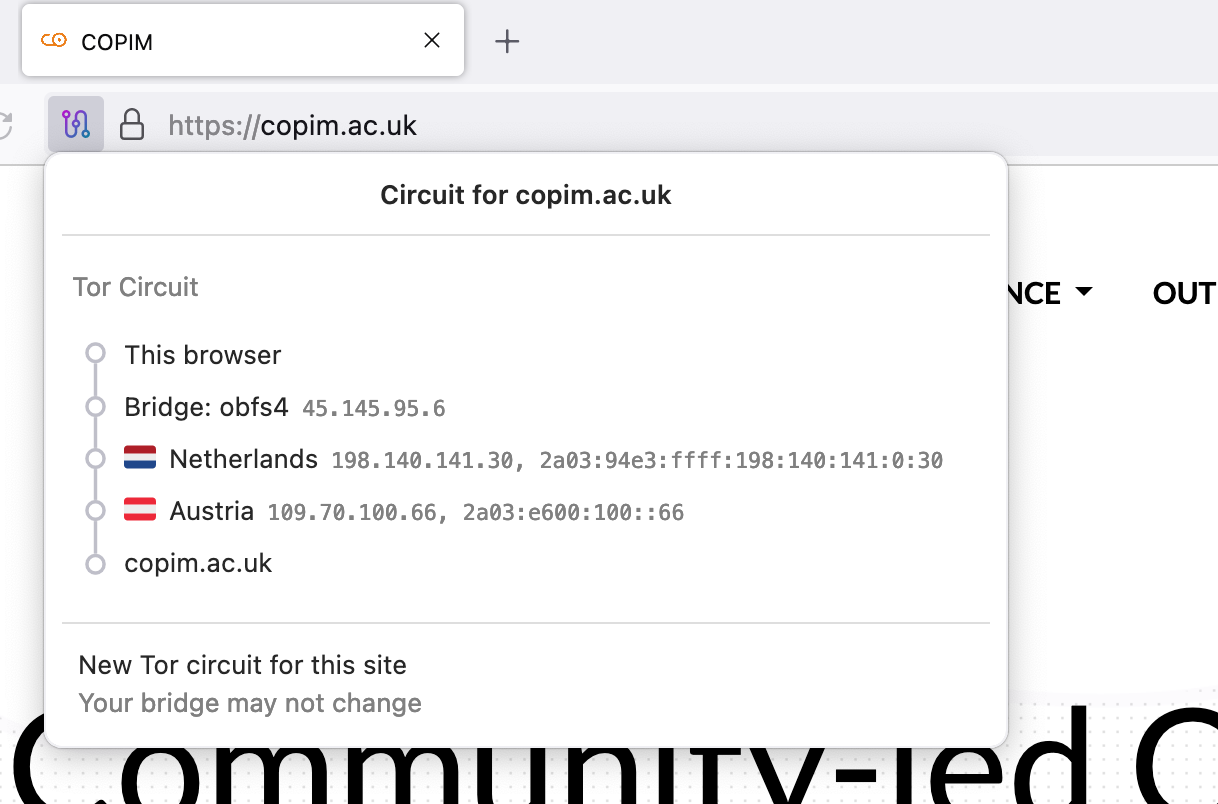
Tor Browser and Tor as a network more generally is how you browse the internet without being monitored. Tor Browser is available for all major operating systems and opens a modified Mozilla Firefox browser that connects you automatically to the Tor network, routing your internet communication through multiple relays so that your IP address is effectively obfuscated. This means that whatever site you look at (or anyone monitoring traffic to that site) cannot determine your uniquely identifiable IP address and thus cannot identify you as an individual as a user of the website. This also allows you to access onion sites which are special websites (or mirrors of websites) only accessible via the Tor network [1]. Tor Browser is released under the Mozilla Public License and developed by the Tor Project.
Tor Browser might be a little heavy-duty for day-to-day internet browsing so you may also want to use LibreWolf. LibreWolf is a security-focused fork of Mozilla Firefox that comes with the uBlock Origin plugin, focuses on privacy-focused search engines like DuckDuckGo, and eschews Mozilla’s recent focus on digital advertising telemetry and “AI” chatbots. By default, it deletes cookies after every session and doesn’t allow canvas access but I personally have turned both those features off for an easier life despite the security risks: if I want to be truly careful, I switch to Tor Browser. LibreWolf is released under the Mozilla Public License and developed by the LibreWolf community.
In addition to LibreWolf’s defaults, I have also installed a selection of the following privacy-focused Firefox plugins [2]:
- Privacy Possum is a fork of Privacy Badger focused on costing companies as much money as possible. It reduces and falsifies the data that tracking cookies send to companies from your browser.
- AdNauseum not only hides ads but continually 'clicks' on every one to screw up their analytics and cost pay-per-click advertisers more money.
- TrackMeNot automatically does randomised nonsense queries to common search engines from your IP to flood any search profile the search engine companies might have on you. Works with Google, Bing, anything with a search bar.
- WhatCampaign changes the analytics parameters in URLs to the string 'FuckOff'.
On my Android phone, I use DuckDuckGo which can be used in place of the default Google search bar to search DuckDuckGo, the search engine that doesn’t track you, and also provides a private browser which blocks hidden trackers on other websites.
NewPipe is an open source YouTube client for Android for watching YouTube without the ads, the tracking, or the extensive permissions that the official YouTube app needs. It allows you to use YouTube, Soundcloud, Bandcamp or media.ccc.de, the video site for the German hacker and information security activist group Chaos Computer Club. YouTube ReVanced for Android is also apparently pretty good for basically the same thing and YouTube++ is a similar alternative for iOS but I use NewPipe. NewPipe is released under the GPL 3.0 license and developed by Team NewPipe.
passwords
Password management is a practice more than any one piece of software and is just something you have to teach yourself to do through habit. There are various solutions for this but the main things are a. do not use the same password for every site and service and b. do not store your passwords in plaintext in a Microsoft Word document or notes file.
KeePassXC and KeePass are open source password management software: KeePass is primarily built for Windows and KeePassXC is a cross-platform fork of a fork of KeePass that works well on Windows, macOS, Linux, and BSD. KeePass and its forks create and open secure database files for passwords which you can store in your file system and make your passwords available to you but inaccessible to adversaries. KeePass is developed by Dominik Reichl and distributed under the GPL-2.0 license; KeePassXC is developed by the KeePassXC Team and distributed under the GPL-2.0 (or 3.0) license.
KeePassXC should be accompanied by the KeePassXC-Browser plugin for LibreWolf [3] or, if you must Mozilla Firefox, Google Chrome or Chromium, and Microsoft Edge [4]. The browser plugin communicates with KeePassXC open on your desktop to allow you to use the passwords stored in your KeePass database without using the in-built password managers in Google Chrome or Mozilla Firefox.
file storage
VeraCrypt is free and open source disk encryption software. It lets you create encrypted and password-protected storage disks in Windows, macOS, and Linux: these storage disks appear like ordinary files but when opened and decrypted with VeraCrypt expand into drives that can store files like any other drives. I have VeraCrypt disks on each of my computers and use them to store private key files and KeePass databases. VeraCrypt also allows you to make encrypted disks on external hard drives like USB sticks so I also have an encrypted disk on USB with a backup of my important private files. VeraCrypt is distributed under the Apache License 2.0 and TrueCrypt License 3.0 and is developed by IDRIX.
taking it further
The recommendations so far should deal with most day-to-day digital security issues but there’s a lot of scope for going further especially if you’re getting involved in leftist anti-fascist or anti-capitalist political organising. The following are some quick suggestions for further investigation should that apply to you:
- Don’t trust any WiFi network. Mobile data hotspots with burner SIM cards for data are more secure but obviously more temporary.
- Don't use email for secure communication. Although email can be made secure with PGP, it's a lot of work for not very much gain. Proton Mail offers encrypted email that is pretty good but, as a rule of thumb, don't send anything that you want to remain secure from any email provider. Assume that your work emails are being read by your employers and do not use your work email address for union organising.
- Look into using mobile Raspberry Pi servers rather than Virtual Private Servers looked after by someone else. If you need the computing power of a less mobile server, look into privacy-focused providers like Njalla.
- Create and carry a Tails portable operating system on a USB stick. Tails is a Debian-based Linux operating system that connects to the internet through the Tor network and that you boot from a USB stick on any computer that you’re able to restart to reach the boot menu. By default, Tails never writes to the hard drive and leaves no digital footprint. It comes with a suite of open source security software including several of the tools discussed in this post.
conclusion
These are scary and unstable times and it can feel scary to not be able to rely on the big companies that you’ve trusted so much of your digital life to. But setting up a suite of security-focused software and making sure that fascists and corporations can’t access your personal data lets you take control in a small way that pushes back against their hegemony.
Several of the websites I manage have onionised versions. I wrote a little about this on PubPub in relation to the Copim website and generally think it should be standard practice for website hosts to offer onion mirrors for those users in countries where they would otherwise be unable to access the clearnet version of the site. ↩︎
Note that some of these plugins may conflict with one another in ways that limit their effectiveness. ↩︎
There’s actually a little extra work to get KeePassXC-Browser working on LibreWolf and there’s instructions here: https://www.reddit.com/r/LibreWolf/comments/1bccgdo/librewolf_linux_with_keepassxc_browser_integration/. ↩︎
Don’t use Microsoft Edge, have some self-respect. ↩︎